'FREAK' flaw undermines security for Apple and Google users, researchers discover By Craig Timberg
March 3, 2015
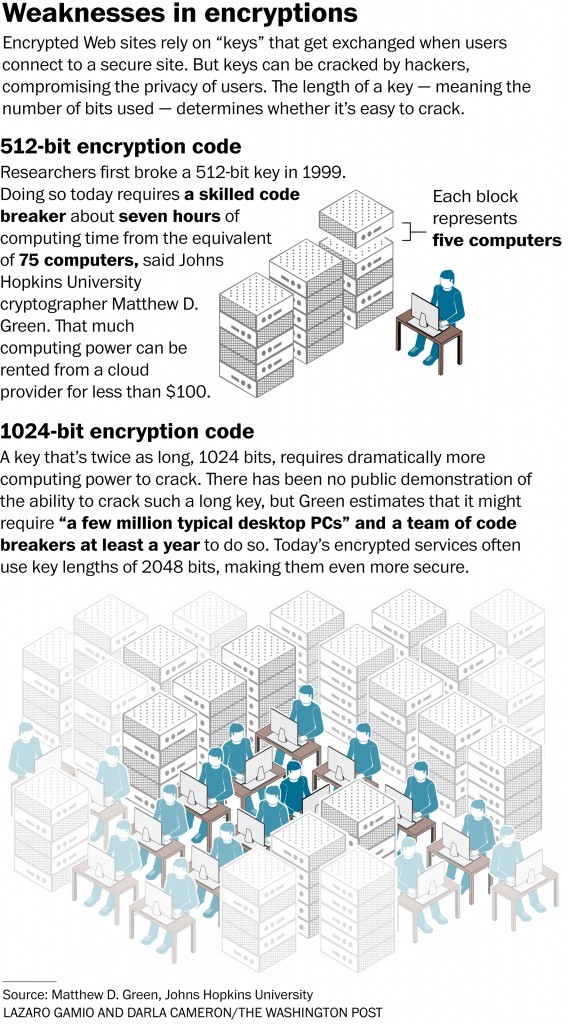
Technology companies are scrambling to fix a major security flaw that for more than a decade left users of Apple and Google devices vulnerable to hacking when they visited millions of supposedly secure Web sites, including Whitehouse.gov, NSA.gov and FBI.gov. The flaw resulted from a former U.S. government policy that forbade the export of strong encryption and required that weaker "export-grade" products be shipped to customers in other countries, say the researchers who discovered the problem. These restrictions were lifted in the late 1990s, but the weaker encryption got baked into widely used software that proliferated around the world and back into the United States, apparently unnoticed until this year. Researchers discovered in recent weeks that they could force browsers to use the weaker encryption, then crack it over the course of just a few hours. Once cracked, hackers could steal passwords and other personal information and potentially launch a broader attack on the Web sites themselves by taking over elements on a page, such as a Facebook "Like" button. The problem illuminates the danger of unintended security consequences at a time when top U.S. officials, frustrated by increasingly strong forms of encryption on smartphones, have called for technology companies to provide "doors" into systems to protect the ability of law enforcement and intelligence agencies to conduct surveillance. Matthew D. Green, a Johns Hopkins cryptographer who helped investigate the encryption flaw, [1] said any requirement to weaken security adds complexity that hackers can exploit. "You're going to add gasoline onto a fire," said Green. "When we say this is going to make things weaker, we're saying this for a reason." Christopher Soghoian, principal technologist for the ACLU, said "You cannot have a secure and an insecure mode at the same time... What we've seen is that those flaws will ultimately impact all users." The existence of the problem with export-grade encryption amazed the researchers, who have dubbed the flaw "FREAK" for Factoring attack on RSA-EXPORT Keys. The export-grade encryption had 512 bits, the maximum allowed under U.S. restrictions designed to limit trade in military technologies in the 1990s, during a an era often called "The Crypto Wars" because of pitched political battles over deploying cryptographic algorithms that even advanced government computers had trouble cracking. But 512-bit cryptography has been considered unacceptably weak for more than a decade. Even experts thought it had disappeared. "We thought of course people stopped using it," said Karthikeyan Bhargavan, a researcher at the French computer science lab INRIA whose team initially found the problem during testing of encryption systems. Nadia Heninger, a University of Pennsylvania cryptographer, said, "This is basically a zombie from the '90s." For vulnerable sites, Heninger found that she could crack the export-grade encryption key in about seven hours, using computers on Amazon Web services. This would allow hackers to conduct what experts call a "man-in-the-middle" attack to make seemingly encrypted traffic easy to read. Such attacks can be launched by anybody who has access to Internet traffic, including governments, Internet providers and coffee shops or airports that offer wifi hotspots. More than one third of encrypted Web sites – including those bearing the "lock" icon that signifies a connection secured by SSL technology – proved vulnerable to attack in recent tests conducted by University of Michigan computer science researchers J. Alex Halderman and Zakir Durumeric. The list [2] includes news organizations, retailers and financial services sites such as americanexpress.com. Of the 14 million Web sites worldwide that offer encryption, more than 5 million remained vulnerable as of Tuesday morning, Halderman said. There is no way to know how widely the FREAK flaw has been used to hack Internet users, though "man-in-the-middle attacks" are popular among governments conducting online surveillance, particularly in their own countries, such as Iran and China. Travelers also are vulnerable whenever they log onto the Internet from a hotel, for example. Green and the other researchers have been alerting affected government agencies and companies over the past several weeks in hopes that they could correct the problem before it became public. Akamai, a leading cloud services company, however reported on efforts it had made to mitigate the problem in a blog post Monday afternoon, bringing attention to the issue earlier than the researchers had planned. In recent days, FBI.gov and Whitehouse.gov have been fixed, though NSA.gov remains vulnerable, said Green. Apple is preparing a security patch that will be in place next week for both its computers and its mobile devices, said company spokeswoman Trudy Miller. Google's Chrome browser is not vulnerable to the FREAK bug, but the browser that comes built into most Android devices is vulnerable. Connections to Google's search Web site are not affected by the flaw. The company said Tuesday that it has developed a patch for the Android operating system's browser and has provided it to "partners," meaning the companies that make most Android devices. It will be up to those companies to deploy it. Security experts have long complained that crucial updates can take months – or never arrive at all – because Google does not control the process of delivering patches to devices running Android.
 [1] http://blog.cryptographyengineering.com/2015/03/attack-of-week-freak-or-factoring-nsa.html
[2] https://www.freakattack.com/
[1] http://blog.cryptographyengineering.com/2015/03/attack-of-week-freak-or-factoring-nsa.html
[2] https://www.freakattack.com/