NSA's Prism surveillance program: how it works and what it can do
Slide from secret PowerPoint presentation describes how program collects data 'directly from the servers' of tech firms James Ball
8 June 2013
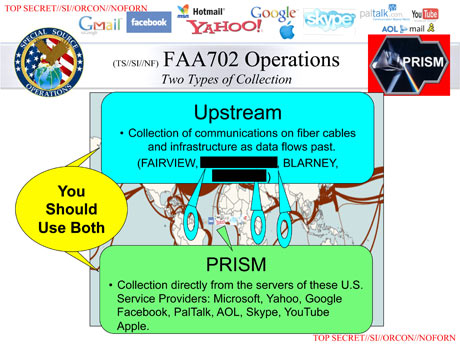 The slide details different methods of data collection under the FISA Amendment Act.
The slide details different methods of data collection under the FISA Amendment Act.Since Prism was first revealed by the Guardian and the Washington Post, there has been much discussion across the media around exactly what the NSA's top-secret program is, how it works, and what it covers. While many of these have provided useful insight and detail into the operation of the program, several of the reports do not tally with the information obtained by the Guardian. Some articles have claimed that Prism is not a tool used for the collection of information from US companies, but is instead an internal tool used to analyse such information. Others have speculated -- in the light of denials from technology companies about granting "direct access" to servers -- that Prism operates through interception of communication cables. Both of these theories appear to be contradicted by internal NSA documents. In the interests of aiding the debate over how Prism works, the Guardian is publishing an additional slide from the 41-slide presentation which details Prism and its operation. We have redacted some program names. The slide details different methods of data collection under the FISA Amendment Act of 2008 (which was renewed in December 2012). It clearly distinguishes Prism, which involves data collection from servers, as distinct from four different programs involving data collection from "fiber cables and infrastructure as data flows past". Essentially, the slide suggests that the NSA also collects some information under FAA702 from cable intercepts, but that process is distinct from Prism. Analysts are encouraged to use both techniques of data gathering. The Guardian's initial reporting of Prism made clear the technology companies denied all knowledge of the program, and did not speculate on whether it would need such co-operation in order to work. A far fuller picture of the exact operation of Prism, and the other surveillance operations brought to light, is expected to emerge in the coming weeks and months, but this slide gives a clearer picture of what Prism is -- and, crucially, isn't.