https://firstlook.org/theintercept/2014/08/12/nprs-dina-temple-raston-passed-cia-funded-nsa-contractor-independent-fear-monger-snowden-reporting/ NPR Is Laundering CIA Talking Points to Make You Scared of NSA Reporting By Glenn Greenwald and Andrew Fishman 12 Aug 2014 On August 1, NPR's Morning Edition broadcast a story [1] by NPR national security reporter Dina Temple-Raston touting explosive claims from what she called "a tech firm based in Cambridge, Massachusetts." That firm, Recorded Future, worked together with "a cyber expert, Mario Vuksan, the CEO of ReversingLabs," to produce a new report [2] that purported to vindicate the repeated accusation from U.S. officials [3] that "revelations from former NSA contract worker Edward Snowden harmed national security and allowed terrorists to develop their own countermeasures." The "big data firm," reported NPR, says that it now "has tangible evidence" proving the government's accusations. Temple-Raston's four-minute, 12-second story devoted the first 3 minutes and 20 seconds to uncritically repeating the report's key conclusion that "just months after the Snowden documents were released, al-Qaeda dramatically changed the way its operatives interacted online" and, post-Snowden, "al-Qaeda didn't just tinker at the edges of its seven-year-old encryption software; it overhauled it." The only skepticism in the NPR report was relegated to 44 seconds at the end when she quoted security expert Bruce Schneier, who questioned the causal relationship between the Snowden disclosures and the new terrorist encryption programs, as well as the efficacy of the new encryption. With this report, Temple-Raston seriously misled NPR's millions of listeners. To begin with, Recorded Future, the outfit that produced the government-affirming report, is anything but independent. To the contrary, it is funded by the CIA and U.S. intelligence community with millions of dollars. [4] Back in 2010, it also filed forms [5] to become a vendor for the NSA. (In response to questions from The Intercept, the company's vice president Jason Hines refused to say whether it works for the NSA, telling us that we should go FOIA that information if we want to know. But according to public reports, [6] Recorded Future "earns most of its revenue from selling to Wall Street quants and intelligence agencies.") The connection between Recorded Future and the U.S. intelligence community is long known. Back in July, 2010, Wired's Noah Shachtman revealed that the company is backed by both "the investment arms of the CIA and Google." Indeed, In-Q-Tel--the deep-pocket investment arm [7] of both the CIA and other intelligence agencies (including the NSA)--has seats on Recorded Future's board of directors and, on its website, lists Recorded Future as one of the companies in its "portfolio." [8] In stark contrast to NPR, The New York Times noted [9] these connections when reporting on the firm in 2011: "Recorded Future is financed with $8 million from the likes of Google's venture arm and In-Q-Tel, which makes investments to benefit the United States intelligence community, and its clients have included government agencies and banks." Worse, Temple-Raston knows all of this. Back in 2012, NPR's Morning Edition broadcast her profile [10] of Recorded Future and its claimed ability [11] to predict the future [12] by gathering internet data. At the end of her report, she noted that the firm has "at least two very important financial backers: the CIA's investment arm, called In-Q-Tel, and Google Ventures. They have reportedly poured millions into the company." That is the company she's now featuring as some sort of independent source that can credibly vindicate the claims of U.S. officials about how Snowden reporting helps terrorists. Beyond all that, the "cyber expert" who Temple-Raston told NPR listeners was "brought in" by Recorded Future to "investigate" these claims--Mario Vuksan, the CEO of ReversingLabs--has his own significant financial ties to the U.S. intelligence community. In 2012, In-Q-Tel proudly touted [13] a "strategic partnership" with ReversingLabs to develop new technology for the Department of Homeland Security. Vuskan hailed the partnership [14] as vital to his company's future prospects. If one wants to argue that a government-mimicking report from a company that is funded by the CIA, and whose board is composed in part of its investment arm, and which centrally relies on research from another CIA partner is somehow newsworthy--fine, one can have that debate. But to pass it off as some sort of independent analysis without even mentioning those central ties is reckless and deceitful--especially when, as is true here, the reporter doing it clearly knows about those ties. Beyond all these CIA connections, the conclusion touted in the NPR report--that al-Qaeda developed more sophisticated encryption techniques due to the Snowden reporting--is dubious in the extreme. It is also undercut by documents contained in the Snowden archive. The Recorded Future "report"--which was actually nothing more than a short blog post [15]--is designed to bolster the year-long fear-mongering campaign of U.S. [16] and British officials arguing [17] that terrorists would realize the need to hide their communications and develop effective means of doing so by virtue of the Snowden reporting. Predictably, former NSA General Counsel Stewart Baker promptly seized on the report (still concealing the firm's CIA connections from readers) to argue in The Washington Post [18] that "the evidence is mounting that Edward Snowden and his journalist allies have helped al-Qaeda improve their security against NSA surveillance." But actual terrorists--long before the Snowden reporting--have been fixated on developing encryption methods and other techniques to protect their communications from electronic surveillance. And they have succeeded in a quite sophisticated manner. One document found in the GCHQ archive provided by Snowden is a 45-page, single-spaced manual that the British spy agency calls a "Jihadist Handbook." Though undated, the content suggests it was originally written in 2002 or 2003: more than 10 years before the Snowden reporting began. It appears to have been last updated shortly after September 2003, and translated into English by GCHQ sometime in 2005 or 2006. Much of it is found online [19] in Arabic. The handbook appears to be an excerpt from a 268-page document called "Abu Zubaydah's Encyclopedia." [20] The encyclopedia, uploaded in Arabic to the internet in 2011, describes itself as the "cumulative result of efforts of the brothers who walked on the path of jihad" and contains highly specific and sophisticated instructions for avoiding electronic surveillance. The first section of the decade-old handbook is entitled "The General Security for all Means of Communication" and includes directions on how to keep landline and mobile telephone calls, emails, and online chats secure. It also includes a detailed discussion of how SIM cards in cell phones can be used by the NSA as tracking devices: exactly the subject of the very first story The Intercept ever published [21] from the Snowden material. The manual further instructs operatives that merely turning off one's cell phone is insufficient to avoid tracking; instead, it instructs, both the battery and SIM card must be removed. It extensively describes how code words should be used for all online communications. So sophisticated is the 10-year-old "Jihadist Manual" that, in many sections, it is virtually identical to the GCHQ's own manual, [22] developed years later (in 2010), for instructing its operatives how to keep their communications secure:
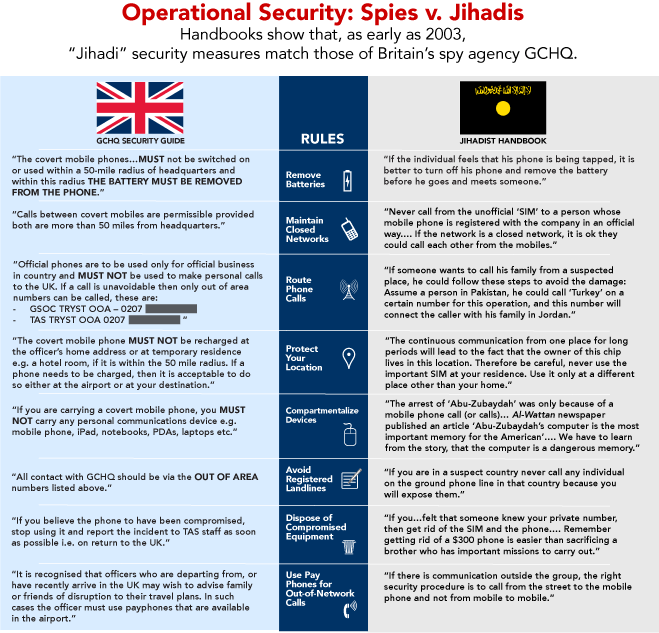 Long before the Snowden reporting, then, those considered by the U.S. to be "terrorists" have been fixated on avoiding electronic surveillance, which is why Osama bin Laden communicated only through personal courier. [23] The "Jihadist Handbook" demonstrates how widespread and sophisticated these techniques have been for many years (GCHQ declined to respond beyond its routine boilerplate claiming that its operations are legal, which has nothing to do with this story).
Then there are the glaring and self-evident fallacies in the report itself. The principal claim on which its conclusion is based is the chronology [24] that extremist groups announced a roll-out of "the first Islamic encryption software for mobiles" in September, 2013 (3 months after the first Snowden report), followed by a new encryption product in December ("The Mujahid's Security").
But it should go without saying that this proves nothing about causation; it is a basic logical principle [25] that "A precedes B" is not evidence that "A caused B." The original Recorded Future report literally did nothing more than assert that there were visible encryption improvements from al-Qaeda that post-dated the first Snowden story, and then, based on no evidence, just asserted the causal link.
Beyond that obvious post hoc ergo propter hoc fallacy, there is no question that "jihadists" have been working for years on sophisticated tactics for communications security; the fact that they continued to be after the Snowden reporting began literally proves nothing.
Indeed, in September of last year, The New York Times made clear [26] that the "jihadists" began developing their own advanced encryption methods years before the start of the Snowden reporting:
Long before the Snowden reporting, then, those considered by the U.S. to be "terrorists" have been fixated on avoiding electronic surveillance, which is why Osama bin Laden communicated only through personal courier. [23] The "Jihadist Handbook" demonstrates how widespread and sophisticated these techniques have been for many years (GCHQ declined to respond beyond its routine boilerplate claiming that its operations are legal, which has nothing to do with this story).
Then there are the glaring and self-evident fallacies in the report itself. The principal claim on which its conclusion is based is the chronology [24] that extremist groups announced a roll-out of "the first Islamic encryption software for mobiles" in September, 2013 (3 months after the first Snowden report), followed by a new encryption product in December ("The Mujahid's Security").
But it should go without saying that this proves nothing about causation; it is a basic logical principle [25] that "A precedes B" is not evidence that "A caused B." The original Recorded Future report literally did nothing more than assert that there were visible encryption improvements from al-Qaeda that post-dated the first Snowden story, and then, based on no evidence, just asserted the causal link.
Beyond that obvious post hoc ergo propter hoc fallacy, there is no question that "jihadists" have been working for years on sophisticated tactics for communications security; the fact that they continued to be after the Snowden reporting began literally proves nothing.
Indeed, in September of last year, The New York Times made clear [26] that the "jihadists" began developing their own advanced encryption methods years before the start of the Snowden reporting:
Al Qaeda's use of advanced encryption technology dates to 2007, when the Global Islamic Media Front released the Asrar al-Mujahedeen, or so-called "Mujahedeen Secrets," software. An updated version, Mujahedeen Secrets 2, was released in January 2008, and has been revised at least twice, most recently in May 2012, analysts said. The program was popularized in the first issue of Inspire, Al Qaeda in the Arabian Peninsula's quarterly online magazine, in a July 2010 post entitled "How to Use Asrar al-Mujahedeen: Sending and Receiving Encrypted Messages."Since then, each issue of Inspire has offered a how-to section on encrypting communications, recommending MS2 as the main encryption tool. All the way back in February, 2001, USA Today reported [27] that al-Qaeda and other groups have been using "uncrackable encryption" since the mid-1990s; the 2001 article stated: "encryption has become the everyday tool of Muslim extremists in Afghanistan, Albania, Britain, Kashmir, Kosovo, the Philippines, Syria, the USA, the West Bank and Gaza and Yemen, U.S. officials say." As has long been clear, "the terrorists" did not need Snowden reporting to know that the U.S. and its partners are doing everything possible to monitor their communications. It is certainly possible that some extremists, like ordinary users all over the world, [28] are more conscious now than before about the need to secure their communications--just as some extremists became aware of interrogation techniques they may face if detained by virtue of reporting on American torture (which is why torture advocates argued [29] that such reporting also helped terrorists). But the key revelation of the Snowden reporting is that the surveillance system built in secret by the NSA and its partners is directed at hundreds of millions of ordinary people [30] and entire populations [31] rather than "the terrorists." Responding to one of the criticisms about the glaring flaws in its report (the obvious absence of causation evidence), Recorded Future admits [32] that "in 2007 Al-Qaeda (AQ) had one encryption product (Asrar) for one platform (PC) which has since been periodically updated (e.g. in 2008)." They claim there was a "significant uptick" after the Snowden reporting but still offer no evidence of a causal connection nor any explanation as to what "the terrorists" learned from those reports that could help them better safeguard their communications or that would provide added motivation to shield those communications. Critically, even if one wanted to accept Recorded Future's timeline as true, there are all sorts of plausible reasons other than Snowden revelations why these groups would have been motivated to develop new encryption protections. One obvious impetus is the August 2013 government boasting to McClatchy [33] (and The Daily Beast [34]) that the State Department ordered the closing of 21 embassies because of what it learned from an intercepted "conference call" among Al Qaeda leaders:
An official who'd been briefed on the matter in Sanaa, the Yemeni capital, told McClatchy that the embassy closings and travel advisory were the result of an intercepted communication between Nasir al-Wuhayshi, the head of the Yemen-based Al Qaida in the Arabian Peninsula, and al Qaida leader Ayman al Zawahiri in which Zawahiri gave "clear orders" to al-Wuhaysi, who was recently named al Qaida's general manager, to carry out an attack.As The Daily Beast put it: "Al-Qaeda leaders had assumed the conference calls, which give Zawahiri the ability to manage his organization from a remote location, were secure. But leaks about the original intercepts have likely exposed the operation that allowed the U.S. intelligence community to listen in on the al-Qaeda board meetings." It does the U.S. government no good to attribute these new encryption efforts to leaks from the U.S. government itself. Recorded Future thus ignores that possibility altogether and suggests--with absolutely no evidence--that it was due to Snowden revelations. They do so even though The New York Times reported [35] a month after the "conference call" leak that "senior officials have made a startling finding: the impact of a leaked terrorist plot by Al Qaeda in August has caused more immediate damage to American counterterrorism efforts than the thousands of classified documents disclosed by Edward Snowden." The NYT added: "The drop in message traffic after the communication intercepts contrasts with what analysts describe as a far more muted impact on counterterrorism efforts from the disclosures by Mr. Snowden of the broad capabilities of N.S.A. surveillance programs." Then there's the completely unproven yet vital assumption that this series of events--even if they happened this way--actually helped the terrorists evade monitoring. Bruce Schneier, the security expert quoted at the end of the NPR report, thinks exactly the opposite is true. He notes numerous journalists, in the wake of the report, asked him "how this will adversely affect US intelligence efforts," and he explained: [36]
I think the reverse is true. I think this will help US intelligence efforts. Cryptography is hard, and the odds that a home-brew encryption product is better than a well-studied open-source tool is slight. Last fall, Matt Blaze said to me that he thought that the Snowden documents will usher in a new dark age of cryptography, as people abandon good algorithms and software for snake oil [37] of their own devising. My guess is that this an example of that.Chris Soghoian, technologist for the ACLU (whose lawyers represent Snowden) noted that these types of stories have been emerging long before Snowden reporting, telling The Intercept: "every few years, a think tank or security company puts out a report on the use of bespoke encryption software by terrorists, and then media eats it up." In the wake of such criticism, Recorded Future issued a supplement to its report, [38] this time claiming that the terrorists "are not using home-brew crypto algorithms" but rather "off the shelf" methods of cryptography. But like Schneier, Soghoian suggested that the developments claimed by Recorded Future would make it easier, not harder, for the U.S. government to monitor the communications of extremists:
If we assume that these programs are developed and distributed by jihadist sympathizers, and not an intelligence service, then the fact that they continue to develop new encryption tools and advocate their use is only further evidence that they don't really know what they're doing. Using terrorist-specific encryption tools will only attract the attention of intelligence agencies. If smart terrorists are using encryption, they're likely using tools like Tor and PGP, the same tools used by government agencies, corporations, journalists, activists and security experts.Then there are the bizarre implications from embracing the claims of the Recorded Future report. For years, both privacy advocates and experts in cryptography have published guides [39] for how internet users can protect the privacy of their online activities [40] using encryption programs such as PGP email [41] and Tor. Recorded Future claims that terrorist groups are using "open source" and "off the shelf" encryption to shield their communications: does that mean that anyone who publishes information on encryption is guilty of helping the terrorists? In sum, Recorded Future is a CIA-dependent company devoted to spreading pro-government propaganda, no matter how absurd. Among its lowlights is its boasting of how it monitored media coverage of Occupy Wall Street, [42] whereby it claimed to detect Iran's "growing influence" over that coverage: "We recently Tweeted a shared link showing coverage and gaining online momentum for the Occupy Wall Street movement. When we look more carefully at influencers in this discussion using our Influencer Map, we find that Iran Press TV is the second largest influencer after the US Media!" None of these serious doubts, fallacies, or questions about this company and its "report" were even alluded to by Temple-Raston in her NPR story, beyond a cursory and very limited Schneier quote tacked onto the end. It's hardly surprising that these kinds of firms, linked to and dependent on the largesse of the U.S. intelligence community, produce pro-government tripe of this sort. That's their function. It's the job of media outlets to scrutinize these claims, not mindlessly repeat and then glorify them as NPR did here. Nadine Chalak contributed additional reporting to this article. [1] http://www.npr.org/blogs/thetwo-way/2014/08/01/336958020/big-data-firm-says-it-can-link-snowden-data-to-changed-terrorist-behavior [2] https://www.recordedfuture.com/al-qaeda-encryption-technology-part-1/ [3] http://www.foxnews.com/us/2013/06/26/al-qaida-other-militants-said-to-be-changing-procedures-to-avoid-surveillance/ [4] http://www.wired.com/2010/07/exclusive-google-cia/ [5] http://www.scribd.com/doc/53042529/NSA-s-ARC-Entry-For-Recorded-Future [6] http://www.businessinsider.com/exclusive-the-first-qa-with-the-ceo-of-the-future-mapping-company-backed-by-google-and-the-cia-2011-3 [7] http://www.foxbusiness.com/technology/2013/06/14/in-q-tel-glimpse-inside-cias-venture-capital-arm/ [8] https://www.iqt.org/portfolio/ [9] http://bits.blogs.nytimes.com/2011/11/17/crushing-the-cost-of-predicting-the-future/ [10] http://www.npr.org/2012/10/08/162397787/predicting-the-future-fantasy-or-a-good-algorithm [11] https://www.recordedfuture.com/christopher-ahlberg-tedxcambridge/ [12] http://www.boston.com/business/technology/innoeco/2010/02/recorded_future_its_like_googl.html [13] https://www.iqt.org/reversinglabs-and-iqt-enter-into-strategic-partnership/ [14] http://www.darkreading.com/risk-management/cia-hunts-for-malware-in-binary-code/d/d-id/1102890 [15] https://www.recordedfuture.com/al-qaeda-encryption-technology-part-2/ [16] http://www.foxnews.com/us/2013/06/26/al-qaida-other-militants-said-to-be-changing-procedures-to-avoid-surveillance/ [17] http://www.dailymail.co.uk/news/article-2616032/Snowden-leaks-mean-terrorists-changing-tactics-slip-radar-GCHQs-workings-revealed.html [18] http://www.washingtonpost.com/news/volokh-conspiracy/wp/2014/08/03/as-evidence-mounts-its-getting-harder-to-defend-edward-snowden/ [19] http://www.shabakataljahad.com/vb/showthread.php?t=7835 [20] https://archive.org/details/Abo_ZoBiDa [21] https://firstlook.org/theintercept/article/2014/02/10/the-nsas-secret-role/ [22] https://firstlook.org/theintercept/document/2014/08/12/gchq-covert-mobile-phones-policy/ [23] http://abcnews.go.com/Blotter/courier-hid-osama-bin-laden/story?id=13528409 [24] https://www.recordedfuture.com/assets/snowden-disclosure-impact-timeline-updated.png [25] http://www.oxfordreference.com/view/10.1093/oi/authority.20110803100339479 [26] http://www.nytimes.com/2013/09/30/us/qaeda-plot-leak-has-undermined-us-intelligence.html [27] http://usatoday30.usatoday.com/tech/news/2001-02-05-binladen.htm [28] http://www.wired.com/2014/05/sandvine-report/ [29] http://www.aei.org/article/foreign-and-defense-policy/regional/india-pakistan-afghanistan/remarks-by-richard-b-cheney/ [30] http://www.theguardian.com/world/2013/jun/06/nsa-phone-records-verizon-court-order [31] http://www.theguardian.com/commentisfree/2013/jul/07/nsa-brazilians-globo-spying [32] https://www.recordedfuture.com/al-qaeda-encryption-technology-reaction/ [33] http://www.mcclatchydc.com/2013/08/04/198521/embassy-closings-travel-warning.html [34] http://www.thedailybeast.com/articles/2013/08/07/al-qaeda-conference-call-intercepted-by-u-s-officials-sparked-alerts.html [35] http://www.nytimes.com/2013/09/30/us/qaeda-plot-leak-has-undermined-us-intelligence.html [36] https://www.schneier.com/blog/archives/2014/05/new_al_qaeda_en_1.html [37] https://www.schneier.com/crypto-gram-9902.html#snakeoil [38] https://www.recordedfuture.com/al-qaeda-encryption-technology-part-2/ [39] http://lifehacker.com/180878/how-to-encrypt-your-email [40] https://pressfreedomfoundation.org/encryption-works [41] https://www.gnupg.org/gph/en/manual.html [42] https://www.recordedfuture.com/irans-growing-influence-occupy-wall-street-protests/