https://firstlook.org/theintercept/article/2014/05/19/data-pirates-caribbean-nsa-recording-every-cell-phone-call-bahamas/ Data Pirates of the Caribbean: The NSA Is Recording Every Cell Phone Call in the Bahamas By Ryan Devereaux, Glenn Greenwald and Laura Poitras 19 May 2014 The National Security Agency is secretly intercepting, recording, and archiving the audio of virtually every cell phone conversation on the island nation of the Bahamas. According to documents provided by NSA whistleblower Edward Snowden, the surveillance is part of a top-secret system -- code-named SOMALGET -- that was implemented without the knowledge or consent of the Bahamian government. Instead, the agency appears to have used access legally obtained in cooperation with the U.S. Drug Enforcement Administration to open a backdoor to the country's cellular telephone network, enabling it to covertly record and store the "full-take audio" of every mobile call made to, from and within the Bahamas -- and to replay those calls for up to a month. SOMALGET is part of a broader NSA program called MYSTIC, which The Intercept has learned is being used to secretly monitor the telecommunications systems of the Bahamas and several other countries, including Mexico, the Philippines, and Kenya. But while MYSTIC scrapes mobile networks for so-called "metadata" -- information that reveals the time, source, and destination of calls -- SOMALGET is a cutting-edge tool that enables the NSA to vacuum up and store the actual content of every conversation in an entire country. All told, the NSA is using MYSTIC to gather personal data on mobile calls placed in countries with a combined population of more than 250 million people. And according to classified documents, the agency is seeking funding to export the sweeping surveillance capability elsewhere. The program raises profound questions about the nature and extent of American surveillance abroad. The U.S. intelligence community routinely justifies its massive spying efforts by citing the threats to national security posed by global terrorism and unpredictable rival nations like Russia and Iran. But the NSA documents indicate that SOMALGET has been deployed in the Bahamas to locate "international narcotics traffickers and special-interest alien smugglers" -- traditional law-enforcement concerns, but a far cry from derailing terror plots or intercepting weapons of mass destruction. "The Bahamas is a stable democracy that shares democratic principles, personal freedoms, and rule of law with the United States," the State Department concluded in a crime and safety report published last year. "There is little to no threat facing Americans from domestic (Bahamian) terrorism, war, or civil unrest." By targeting the Bahamas' entire mobile network, the NSA is intentionally collecting and retaining intelligence on millions of people who have not been accused of any crime or terrorist activity. Nearly five million Americans visit the country each year, and many prominent U.S. citizens keep homes there, including Sen. Tom Harkin (D-Iowa), Bill Gates, and Oprah Winfrey. In addition, the program is a serious -- and perhaps illegal -- abuse of the access to international phone networks that other countries willingly grant the United States for legitimate law-enforcement surveillance. If the NSA is using the Drug Enforcement Administration's relationship to the Bahamas as a cover for secretly recording the entire country's mobile phone calls, it could imperil the longstanding tradition of international law enforcement cooperation that the United States enjoys with its allies. "It's surprising, the short-sightedness of the government," says Michael German, a fellow at New York University's Brennan Center for Justice who spent 16 years as an FBI agent conducting undercover investigations. "That they couldn't see how exploiting a lawful mechanism to such a degree that you might lose that justifiable access -- that's where the intelligence community is acting in a way that harms its long-term interests, and clearly the long-term national security interests of the United States." The NSA refused to comment on the program, but said in a statement that "the implication that NSA's foreign intelligence collection is arbitrary and unconstrained is false." The agency also insisted that it follows procedures to "protect the privacy of U.S. persons" whose communications are "incidentally collected." Informed about the NSA's spying, neither the Bahamian prime minister's office nor the country's national security minister had any comment. The embassies of Mexico, Kenya, and the Philippines did not respond to phone messages and emails.
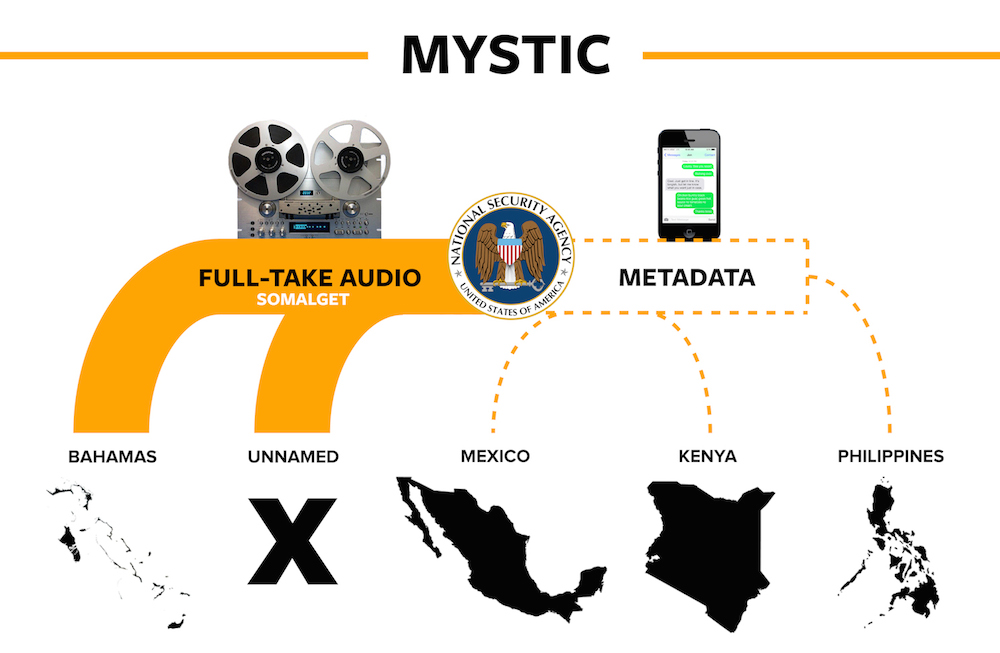 Illustration by Josh Begley
In March, The Washington Post revealed [1] that the NSA had developed the capability to record and store an entire nation's phone traffic for 30 days. The Post reported that the capacity was a feature of MYSTIC, which it described as a "voice interception program" that is fully operational in one country and proposed for activation in six others. (The Post also referred to NSA documents suggesting that MYSTIC was pulling metadata in some of those countries.) Citing government requests, the paper declined to name any of those countries.
The Intercept has confirmed that as of 2013, [2] the NSA was actively using MYSTIC to gather cell-phone metadata in five countries, and was intercepting voice data in two of them. Documents show that the NSA has been generating intelligence reports from MYSTIC surveillance in the Bahamas, Mexico, Kenya, the Philippines, and one other country, which The Intercept is not naming in response to specific, credible concerns that doing so could lead to increased violence. The more expansive full-take recording capability has been deployed in both the Bahamas and the unnamed country.
MYSTIC was established in 2009 by the NSA's Special Source Operations division, which works with corporate partners to conduct surveillance. Documents in the Snowden archive describe it [3] as a "program for embedded collection systems overtly installed on target networks, predominantly for the collection and processing of wireless/mobile communications networks."
Illustration by Josh Begley
In March, The Washington Post revealed [1] that the NSA had developed the capability to record and store an entire nation's phone traffic for 30 days. The Post reported that the capacity was a feature of MYSTIC, which it described as a "voice interception program" that is fully operational in one country and proposed for activation in six others. (The Post also referred to NSA documents suggesting that MYSTIC was pulling metadata in some of those countries.) Citing government requests, the paper declined to name any of those countries.
The Intercept has confirmed that as of 2013, [2] the NSA was actively using MYSTIC to gather cell-phone metadata in five countries, and was intercepting voice data in two of them. Documents show that the NSA has been generating intelligence reports from MYSTIC surveillance in the Bahamas, Mexico, Kenya, the Philippines, and one other country, which The Intercept is not naming in response to specific, credible concerns that doing so could lead to increased violence. The more expansive full-take recording capability has been deployed in both the Bahamas and the unnamed country.
MYSTIC was established in 2009 by the NSA's Special Source Operations division, which works with corporate partners to conduct surveillance. Documents in the Snowden archive describe it [3] as a "program for embedded collection systems overtly installed on target networks, predominantly for the collection and processing of wireless/mobile communications networks."
 A top-secret description of the MYSTIC program written by the NSA's Special Source Operations division
If an entire nation's cell-phone calls were a menu of TV shows, MYSTIC would be a cable programming guide showing which channels offer which shows, and when. SOMALGET would be the DVR that automatically records every show on every channel and stores them for a month. MYSTIC provides the access; SOMALGET provides the massive amounts of storage needed to archive all those calls so that analysts can listen to them at will after the fact. According to one NSA document, [4] SOMALGET is "deployed against entire networks" in the Bahamas and the second country, and processes "over 100 million call events per day."
SOMALGET's capabilities are further detailed in a May 2012 memo [5] written by an official in the NSA's International Crime and Narcotics division. The memo hails the "great success" the NSA's drugs and crime unit has enjoyed through its use of the program, and boasts about how "beneficial" the collection and recording of every phone call in a given nation can be to intelligence analysts.
Rather than simply making "tentative analytic conclusions derived from metadata," the memo notes, analysts can follow up on hunches by going back in time and listening to phone calls recorded during the previous month. Such "retrospective retrieval" means that analysts can figure out what targets were saying even when the calls occurred before the targets were identified. "[W]e buffer certain calls that MAY be of foreign intelligence value for a sufficient period to permit a well-informed decision on whether to retrieve and return specific audio content," the NSA official reported.
"There is little reason," the official added, that SOMALGET could not be expanded to more countries, as long as the agency provided adequate engineering, coordination and hardware. There is no indication in the documents that the NSA followed up on the official's enthusiasm.
A top-secret description of the MYSTIC program written by the NSA's Special Source Operations division
If an entire nation's cell-phone calls were a menu of TV shows, MYSTIC would be a cable programming guide showing which channels offer which shows, and when. SOMALGET would be the DVR that automatically records every show on every channel and stores them for a month. MYSTIC provides the access; SOMALGET provides the massive amounts of storage needed to archive all those calls so that analysts can listen to them at will after the fact. According to one NSA document, [4] SOMALGET is "deployed against entire networks" in the Bahamas and the second country, and processes "over 100 million call events per day."
SOMALGET's capabilities are further detailed in a May 2012 memo [5] written by an official in the NSA's International Crime and Narcotics division. The memo hails the "great success" the NSA's drugs and crime unit has enjoyed through its use of the program, and boasts about how "beneficial" the collection and recording of every phone call in a given nation can be to intelligence analysts.
Rather than simply making "tentative analytic conclusions derived from metadata," the memo notes, analysts can follow up on hunches by going back in time and listening to phone calls recorded during the previous month. Such "retrospective retrieval" means that analysts can figure out what targets were saying even when the calls occurred before the targets were identified. "[W]e buffer certain calls that MAY be of foreign intelligence value for a sufficient period to permit a well-informed decision on whether to retrieve and return specific audio content," the NSA official reported.
"There is little reason," the official added, that SOMALGET could not be expanded to more countries, as long as the agency provided adequate engineering, coordination and hardware. There is no indication in the documents that the NSA followed up on the official's enthusiasm.
 A 2012 memo written by the NSA's International Crime & Narcotics division
The documents don't spell out how the NSA has been able to tap the phone calls of an entire country. But one memo indicates that SOMALGET data is covertly acquired under the auspices of "lawful intercepts" made through Drug Enforcement Administration "accesses"-- legal wiretaps of foreign phone networks that the DEA requests as part of international law enforcement cooperation.
When U.S. drug agents need to tap a phone of a suspected drug kingpin in another country, they call up their counterparts and ask them set up an intercept. To facilitate those taps, many nations -- including the Bahamas -- have hired contractors who install and maintain so-called lawful intercept equipment on their telecommunications. With SOMALGET, it appears that the NSA has used the access those contractors developed to secretly mine the country's entire phone system for "signals intelligence" --recording every mobile call in the country. "Host countries," the document notes, "are not aware of NSA's SIGINT collection."
"Lawful intercept systems engineer communications vulnerabilities into networks, forcing the carriers to weaken," says Christopher Soghoian, the principal technologist for the American Civil Liberties Union. "Host governments really should be thinking twice before they accept one of these Trojan horses."
The DEA has long been in a unique position to help the NSA gain backdoor access to foreign phone networks. "DEA has close relationships with foreign government counterparts and vetted foreign partners," the manager of the NSA's drug-war efforts reported in a 2004 memo. [6] Indeed, with more than 80 international offices, the DEA is one of the most widely deployed U.S. agencies around the globe.
But what many foreign governments fail to realize is that U.S. drug agents don't confine themselves to simply fighting narcotics traffickers. "DEA is actually one of the biggest spy operations there is," says Finn Selander, a former DEA special agent who works with the drug-reform advocacy group Law Enforcement Against Prohibition. "Our mandate is not just drugs. We collect intelligence."
What's more, Selander adds, the NSA has aided the DEA for years on surveillance operations. "On our reports, there's drug information and then there's non-drug information," he says. "So countries let us in because they don't view us, really, as a spy organization."
Selander's first-hand experience is echoed in the 2004 memo by the manager of the NSA's drug-war efforts, which was titled "DEA: The Other Warfighter." The DEA and the NSA "enjoy a vibrant two-way information-sharing relationship," the memo observes, and cooperate so closely on counternarcotics and counterterrorism that there is a risk of "blurring the lines between the two missions."
Still, the ability to record and replay the phone calls of an entire country appears to be a relatively new weapon in the NSA's arsenal. None of the half-dozen former U.S. law enforcement officials interviewed by The Intercept said they had ever heard of a surveillance operation quite like the NSA's Bahamas collection.
"I'm completely unfamiliar with the program," says Joel Margolis, a former DEA official who is now executive vice president of government affairs for Subsentio, a Colorado-based company that installs lawful intercepts for telecommunications providers. "I used to work in DEA's office of chief counsel, and I was their lead specialist on lawful surveillance matters. I wasn't aware of anything like this."
A 2012 memo written by the NSA's International Crime & Narcotics division
The documents don't spell out how the NSA has been able to tap the phone calls of an entire country. But one memo indicates that SOMALGET data is covertly acquired under the auspices of "lawful intercepts" made through Drug Enforcement Administration "accesses"-- legal wiretaps of foreign phone networks that the DEA requests as part of international law enforcement cooperation.
When U.S. drug agents need to tap a phone of a suspected drug kingpin in another country, they call up their counterparts and ask them set up an intercept. To facilitate those taps, many nations -- including the Bahamas -- have hired contractors who install and maintain so-called lawful intercept equipment on their telecommunications. With SOMALGET, it appears that the NSA has used the access those contractors developed to secretly mine the country's entire phone system for "signals intelligence" --recording every mobile call in the country. "Host countries," the document notes, "are not aware of NSA's SIGINT collection."
"Lawful intercept systems engineer communications vulnerabilities into networks, forcing the carriers to weaken," says Christopher Soghoian, the principal technologist for the American Civil Liberties Union. "Host governments really should be thinking twice before they accept one of these Trojan horses."
The DEA has long been in a unique position to help the NSA gain backdoor access to foreign phone networks. "DEA has close relationships with foreign government counterparts and vetted foreign partners," the manager of the NSA's drug-war efforts reported in a 2004 memo. [6] Indeed, with more than 80 international offices, the DEA is one of the most widely deployed U.S. agencies around the globe.
But what many foreign governments fail to realize is that U.S. drug agents don't confine themselves to simply fighting narcotics traffickers. "DEA is actually one of the biggest spy operations there is," says Finn Selander, a former DEA special agent who works with the drug-reform advocacy group Law Enforcement Against Prohibition. "Our mandate is not just drugs. We collect intelligence."
What's more, Selander adds, the NSA has aided the DEA for years on surveillance operations. "On our reports, there's drug information and then there's non-drug information," he says. "So countries let us in because they don't view us, really, as a spy organization."
Selander's first-hand experience is echoed in the 2004 memo by the manager of the NSA's drug-war efforts, which was titled "DEA: The Other Warfighter." The DEA and the NSA "enjoy a vibrant two-way information-sharing relationship," the memo observes, and cooperate so closely on counternarcotics and counterterrorism that there is a risk of "blurring the lines between the two missions."
Still, the ability to record and replay the phone calls of an entire country appears to be a relatively new weapon in the NSA's arsenal. None of the half-dozen former U.S. law enforcement officials interviewed by The Intercept said they had ever heard of a surveillance operation quite like the NSA's Bahamas collection.
"I'm completely unfamiliar with the program," says Joel Margolis, a former DEA official who is now executive vice president of government affairs for Subsentio, a Colorado-based company that installs lawful intercepts for telecommunications providers. "I used to work in DEA's office of chief counsel, and I was their lead specialist on lawful surveillance matters. I wasn't aware of anything like this."
 A 2012 memo written by the NSA's International Crime & Narcotics division
For nearly two decades, telecom providers in the United States have been legally obligated under the 1994 Communications Assistance for Law Enforcement Act to build their networks with wiretapping capabilities, providing law enforcement agencies with access to more efficient, centrally managed surveillance.
Since CALEA's passage, many countries have adopted similar measures, making it easier to gather telecommunications intelligence for international investigations. A 2001 working group for the United Nations Office on Drugs and Crime [7] went so far as to urge countries to consider permitting foreign law enforcement agencies to initiate international wiretaps directly from within their own territories.
The process for setting up lawful intercepts in foreign countries is largely the same as in the United States. "Law enforcement issues a warrant or other authorization, a carrier or a carrier's agent responds to the warrant by provisioning the intercept, and the information is sent in sort of a one-way path to the law enforcement agency," says Marcus Thomas, a former FBI assistant director who now serves as chief technology officer for Subsentio.
When U.S. drug agents wiretap a country's phone networks, they must comply with the host country's laws and work alongside their law enforcement counterparts. "The way DEA works with our allies -- it could be Bahamas or Jamaica or anywhere -- the host country has to invite us," says Margolis. "We come in and provide the support, but they do the intercept themselves."
The Bahamas' Listening Devices Act [8] requires all wiretaps to be authorized in writing either by the minister of national security or the police commissioner in consultation with the attorney general. The individuals to be targeted must be named. Under the nation's Data Protection Act, [9] personal data may only be "collected by means which are both lawful and fair in the circumstances of the case." The office of the Bahamian data protection commissioner, which administers the act, said in a statement that it "was not aware of the matter you raise."
Countries like the Bahamas don't install lawful intercepts on their own. With the adoption of international standards, a thriving market has emerged for private firms that are contracted by foreign governments to install and maintain lawful intercept equipment. Currently valued at more than $128 million, the global market for private interception services is expected to skyrocket to more than $970 million within the next four years, according to a 2013 report [10] from the research firm Markets and Markets.
"Most telecom hardware vendors will have some solutions for legal interception," says a former mobile telecommunications engineer who asked not to be named because he is currently working for the British government. "That's pretty much because legal interception is a requirement if you're going to operate a mobile phone network."
The proliferation of private contractors has apparently provided the NSA with direct access to foreign phone networks. According to the documents, MYSTIC draws its data from "collection systems" that were overtly installed on the telecommunications systems of targeted countries, apparently by corporate "partners" cooperating with the NSA.
One NSA document [11] spells out that "the overt purpose" given for accessing foreign telecommunications systems is "for legitimate commercial service for the Telco's themselves." But the same document adds: "Our covert mission is the provision of SIGINT," or signals intelligence.
The classified 2013 intelligence budget also describes MYSTIC [12] as using "partner-enabled" access to both cellular and landline phone networks. The goal of the access, the budget says, is to "provide comprehensive metadata access and content against targeted communications" in the Caribbean, Mexico, Kenya, the Philippines, and the unnamed country. The budget adds that in the Bahamas, Mexico, and the Philippines, MYSTIC requires "contracted services" for its "operational sustainment."
A 2012 memo written by the NSA's International Crime & Narcotics division
For nearly two decades, telecom providers in the United States have been legally obligated under the 1994 Communications Assistance for Law Enforcement Act to build their networks with wiretapping capabilities, providing law enforcement agencies with access to more efficient, centrally managed surveillance.
Since CALEA's passage, many countries have adopted similar measures, making it easier to gather telecommunications intelligence for international investigations. A 2001 working group for the United Nations Office on Drugs and Crime [7] went so far as to urge countries to consider permitting foreign law enforcement agencies to initiate international wiretaps directly from within their own territories.
The process for setting up lawful intercepts in foreign countries is largely the same as in the United States. "Law enforcement issues a warrant or other authorization, a carrier or a carrier's agent responds to the warrant by provisioning the intercept, and the information is sent in sort of a one-way path to the law enforcement agency," says Marcus Thomas, a former FBI assistant director who now serves as chief technology officer for Subsentio.
When U.S. drug agents wiretap a country's phone networks, they must comply with the host country's laws and work alongside their law enforcement counterparts. "The way DEA works with our allies -- it could be Bahamas or Jamaica or anywhere -- the host country has to invite us," says Margolis. "We come in and provide the support, but they do the intercept themselves."
The Bahamas' Listening Devices Act [8] requires all wiretaps to be authorized in writing either by the minister of national security or the police commissioner in consultation with the attorney general. The individuals to be targeted must be named. Under the nation's Data Protection Act, [9] personal data may only be "collected by means which are both lawful and fair in the circumstances of the case." The office of the Bahamian data protection commissioner, which administers the act, said in a statement that it "was not aware of the matter you raise."
Countries like the Bahamas don't install lawful intercepts on their own. With the adoption of international standards, a thriving market has emerged for private firms that are contracted by foreign governments to install and maintain lawful intercept equipment. Currently valued at more than $128 million, the global market for private interception services is expected to skyrocket to more than $970 million within the next four years, according to a 2013 report [10] from the research firm Markets and Markets.
"Most telecom hardware vendors will have some solutions for legal interception," says a former mobile telecommunications engineer who asked not to be named because he is currently working for the British government. "That's pretty much because legal interception is a requirement if you're going to operate a mobile phone network."
The proliferation of private contractors has apparently provided the NSA with direct access to foreign phone networks. According to the documents, MYSTIC draws its data from "collection systems" that were overtly installed on the telecommunications systems of targeted countries, apparently by corporate "partners" cooperating with the NSA.
One NSA document [11] spells out that "the overt purpose" given for accessing foreign telecommunications systems is "for legitimate commercial service for the Telco's themselves." But the same document adds: "Our covert mission is the provision of SIGINT," or signals intelligence.
The classified 2013 intelligence budget also describes MYSTIC [12] as using "partner-enabled" access to both cellular and landline phone networks. The goal of the access, the budget says, is to "provide comprehensive metadata access and content against targeted communications" in the Caribbean, Mexico, Kenya, the Philippines, and the unnamed country. The budget adds that in the Bahamas, Mexico, and the Philippines, MYSTIC requires "contracted services" for its "operational sustainment."
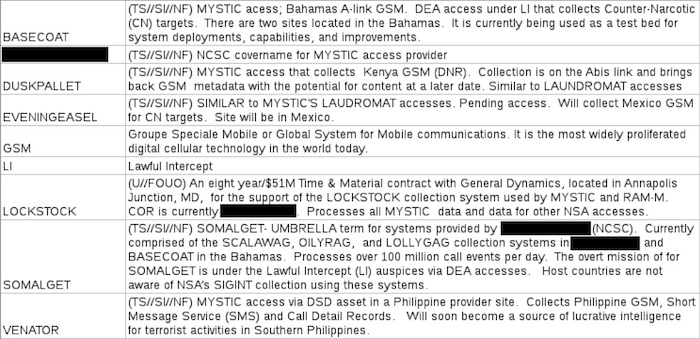 Definitions of terms related to the MYSTIC program, drawn from an NSA glossary
The NSA documents don't specify who is providing access in the Bahamas. But they do describe SOMALGET as an "umbrella term" for systems provided by a private firm, which is described elsewhere in the documents as a "MYSTIC access provider." (The documents don't name the firm, but rather refer to a cover name that The Intercept has agreed not to publish in response to a specific, credible concern that doing so could lead to violence.) Communications experts consulted by The Intercept say the descriptions in the documents suggest a company able to install lawful intercept equipment on phone networks.
Though it is not the "access provider," the behemoth NSA contractor General Dynamics is directly involved in both MYSTIC and SOMALGET. According to documents, the firm has an eight-year, $51 million contract to process "all MYSTIC data and data for other NSA accesses" at a facility in Annapolis Junction, Maryland, down the road from NSA's headquarters. NSA logs of SOMALGET collection activity -- communications between analysts about issues such as outages and performance problems -- contain references to a technician at a "SOMALGET processing facility" who bears the same name as a LinkedIn user listing General Dynamics as his employer. Reached for comment, a General Dynamics spokesperson referred questions to the NSA.
According to the NSA documents, MYSTIC targets calls and other data transmitted on Global System for Mobile Communications networks -- the primary framework used for cell phone calls worldwide. In the Philippines, MYSTIC collects "GSM, Short Message Service (SMS) and Call Detail Records" via access provided by a "DSD asset in a Philippine provider site." (The DSD refers to the Defence Signals Directorate, an arm of Australian intelligence. The Australian consulate in New York declined to comment.) The operation in Kenya is "sponsored" by the CIA, according to the documents, and collects "GSM metadata with the potential for content at a later date." The Mexican operation is likewise sponsored by the CIA. The documents don't say how or under what pretenses the agency is gathering call data in those countries.
In the Bahamas, the documents say, the NSA intercepts GSM data that is transmitted over what is known as the "A link"--or "A interface"--a core component of many mobile networks. The A link transfers data between two crucial parts of GSM networks -- the base station subsystem, where phones in the field communicate with cell towers, and the network subsystem, which routes calls and text messages to the appropriate destination. "It's where all of the telephone traffic goes," says the former engineer.
Punching into this portion of a county's mobile network would give the NSA access to a virtually non-stop stream of communications. It would also require powerful technology.
"I seriously don't think that would be your run-of-the-mill legal interception equipment," says the former engineer, who worked with hardware and software that typically maxed out at 1,000 intercepts. The NSA, by contrast, is recording and storing tens of millions of calls -- "mass surveillance," he observes, that goes far beyond the standard practices for lawful interception recognized around the world.
The Bahamas Telecommunications Company did not respond to repeated phone calls and emails.
If the U.S. government wanted to make a case for surveillance in the Bahamas, it could point to the country's status as a leading haven for tax cheats, corporate shell games, and a wide array of black-market traffickers. The State Department considers the Bahamas both a "major drug-transit country" and a "major money laundering country" (a designation it shares with more than 60 other nations, including the U.S.). According to the International Monetary Fund, as of 2011 the Bahamas was home to 271 banks and trust companies with active licenses. At the time, the Bahamian banks held $595 billion in U.S. assets.
But the NSA documents don't reflect a concerted focus on the money launderers and powerful financial institutions -- including numerous Western banks -- that underpin the black market for narcotics in the Bahamas. Instead, an internal NSA presentation from 2013 recounts with pride how analysts used SOMALGET to locate an individual who "arranged Mexico-to-United States marijuana shipments" through the U.S. Postal Service.
Definitions of terms related to the MYSTIC program, drawn from an NSA glossary
The NSA documents don't specify who is providing access in the Bahamas. But they do describe SOMALGET as an "umbrella term" for systems provided by a private firm, which is described elsewhere in the documents as a "MYSTIC access provider." (The documents don't name the firm, but rather refer to a cover name that The Intercept has agreed not to publish in response to a specific, credible concern that doing so could lead to violence.) Communications experts consulted by The Intercept say the descriptions in the documents suggest a company able to install lawful intercept equipment on phone networks.
Though it is not the "access provider," the behemoth NSA contractor General Dynamics is directly involved in both MYSTIC and SOMALGET. According to documents, the firm has an eight-year, $51 million contract to process "all MYSTIC data and data for other NSA accesses" at a facility in Annapolis Junction, Maryland, down the road from NSA's headquarters. NSA logs of SOMALGET collection activity -- communications between analysts about issues such as outages and performance problems -- contain references to a technician at a "SOMALGET processing facility" who bears the same name as a LinkedIn user listing General Dynamics as his employer. Reached for comment, a General Dynamics spokesperson referred questions to the NSA.
According to the NSA documents, MYSTIC targets calls and other data transmitted on Global System for Mobile Communications networks -- the primary framework used for cell phone calls worldwide. In the Philippines, MYSTIC collects "GSM, Short Message Service (SMS) and Call Detail Records" via access provided by a "DSD asset in a Philippine provider site." (The DSD refers to the Defence Signals Directorate, an arm of Australian intelligence. The Australian consulate in New York declined to comment.) The operation in Kenya is "sponsored" by the CIA, according to the documents, and collects "GSM metadata with the potential for content at a later date." The Mexican operation is likewise sponsored by the CIA. The documents don't say how or under what pretenses the agency is gathering call data in those countries.
In the Bahamas, the documents say, the NSA intercepts GSM data that is transmitted over what is known as the "A link"--or "A interface"--a core component of many mobile networks. The A link transfers data between two crucial parts of GSM networks -- the base station subsystem, where phones in the field communicate with cell towers, and the network subsystem, which routes calls and text messages to the appropriate destination. "It's where all of the telephone traffic goes," says the former engineer.
Punching into this portion of a county's mobile network would give the NSA access to a virtually non-stop stream of communications. It would also require powerful technology.
"I seriously don't think that would be your run-of-the-mill legal interception equipment," says the former engineer, who worked with hardware and software that typically maxed out at 1,000 intercepts. The NSA, by contrast, is recording and storing tens of millions of calls -- "mass surveillance," he observes, that goes far beyond the standard practices for lawful interception recognized around the world.
The Bahamas Telecommunications Company did not respond to repeated phone calls and emails.
If the U.S. government wanted to make a case for surveillance in the Bahamas, it could point to the country's status as a leading haven for tax cheats, corporate shell games, and a wide array of black-market traffickers. The State Department considers the Bahamas both a "major drug-transit country" and a "major money laundering country" (a designation it shares with more than 60 other nations, including the U.S.). According to the International Monetary Fund, as of 2011 the Bahamas was home to 271 banks and trust companies with active licenses. At the time, the Bahamian banks held $595 billion in U.S. assets.
But the NSA documents don't reflect a concerted focus on the money launderers and powerful financial institutions -- including numerous Western banks -- that underpin the black market for narcotics in the Bahamas. Instead, an internal NSA presentation from 2013 recounts with pride how analysts used SOMALGET to locate an individual who "arranged Mexico-to-United States marijuana shipments" through the U.S. Postal Service.
 A slide from a 2013 NSA Special Source Operations presentation
The presentation doesn't say whether the NSA shared the information with the DEA. But the drug agency's Special Operations Divison has come under fire for improperly using classified information obtained by the NSA to launch criminal investigations -- and then creating false narratives to mislead courts about how the investigations began. The tactic -- known as parallel construction -- was first reported by Reuters last year, [13] and is now under investigation by the Justice Department's inspector general. [14]
So: Beyond a desire to bust island pot dealers, why would the NSA choose to apply a powerful collection tool such as SOMALGET against the Bahamas, which poses virtually no threat to the United States?
The answer may lie in a document that characterizes the Bahamas operation as a "test bed for system deployments, capabilities, and improvements" to SOMALGET. The country's small population -- fewer than 400,000 residents -- provides a manageable sample to try out the surveillance system's features. Since SOMALGET is also operational in one other country, the Bahamas may be used as a sort of guinea pig to beta-test improvements and alterations without impacting the system's operations elsewhere.
"From an engineering point of view it makes perfect sense," says the former engineer. "Absolutely."
Beyond the Bahamas, the other countries being targeted by MYSTIC are more in line with the NSA's more commonly touted priorities. In Kenya, the U.S. works closely with local security forces in combating the militant fundamentalist group Al-Shabab, based in neighboring Somalia. In the Philippines, the U.S. continues to support a bloody shadow war against Islamist extremists launched by the Bush administration in 2002. Last month, President Barack Obama visited Manila to sign a military pact guaranteeing that U.S. operations in Southeast Asia will continue and expand for at least another decade.
Mexico, another country targeted by MYSTIC, has received billions of dollars in police, military, and intelligence aid from the U.S. government over the past seven years to fight the war on drugs, a conflict that has left more than 70,000 Mexicans dead by some estimates. Attorney General Eric Holder has described Mexican drug cartels as a U.S. "national security threat," and in 2009, then-CIA director Michael Hayden said the violence and chaos in Mexico would soon be the second greatest security threat facing the U.S. behind Al Qaeda.
A slide from a 2013 NSA Special Source Operations presentation
The presentation doesn't say whether the NSA shared the information with the DEA. But the drug agency's Special Operations Divison has come under fire for improperly using classified information obtained by the NSA to launch criminal investigations -- and then creating false narratives to mislead courts about how the investigations began. The tactic -- known as parallel construction -- was first reported by Reuters last year, [13] and is now under investigation by the Justice Department's inspector general. [14]
So: Beyond a desire to bust island pot dealers, why would the NSA choose to apply a powerful collection tool such as SOMALGET against the Bahamas, which poses virtually no threat to the United States?
The answer may lie in a document that characterizes the Bahamas operation as a "test bed for system deployments, capabilities, and improvements" to SOMALGET. The country's small population -- fewer than 400,000 residents -- provides a manageable sample to try out the surveillance system's features. Since SOMALGET is also operational in one other country, the Bahamas may be used as a sort of guinea pig to beta-test improvements and alterations without impacting the system's operations elsewhere.
"From an engineering point of view it makes perfect sense," says the former engineer. "Absolutely."
Beyond the Bahamas, the other countries being targeted by MYSTIC are more in line with the NSA's more commonly touted priorities. In Kenya, the U.S. works closely with local security forces in combating the militant fundamentalist group Al-Shabab, based in neighboring Somalia. In the Philippines, the U.S. continues to support a bloody shadow war against Islamist extremists launched by the Bush administration in 2002. Last month, President Barack Obama visited Manila to sign a military pact guaranteeing that U.S. operations in Southeast Asia will continue and expand for at least another decade.
Mexico, another country targeted by MYSTIC, has received billions of dollars in police, military, and intelligence aid from the U.S. government over the past seven years to fight the war on drugs, a conflict that has left more than 70,000 Mexicans dead by some estimates. Attorney General Eric Holder has described Mexican drug cartels as a U.S. "national security threat," and in 2009, then-CIA director Michael Hayden said the violence and chaos in Mexico would soon be the second greatest security threat facing the U.S. behind Al Qaeda.The legality of the NSA's sweeping surveillance in the Bahamas is unclear, given the permissive laws under which the U.S intelligence community operates. Earlier this year, President Obama issued a policy directive [15] imposing "new limits" on the U.S. intelligence community's use of "signals intelligence collected in bulk." In addition to threats against military or allied personnel, the directive lists five broad conditions under which the agency would be permitted to trawl for data in unrestricted dragnets: threats posed by foreign powers, terrorism, weapons of mass destruction, cybersecurity, and "transnational criminal threats, including illicit finance and sanctions evasion." SOMALGET operates under Executive Order 12333, [16] a Reagan-era rule establishing wide latitude for the NSA and other intelligence agencies to spy on other countries, as long as the attorney general is convinced the efforts are aimed at gathering foreign intelligence. In 2000, the NSA assured Congress [17] that all electronic surveillance performed under 12333 "must be conducted in a manner that minimizes the acquisition, retention, and dissemination of information about unconsenting U.S. persons." In reality, many legal experts point out, the lack of judicial oversight or criminal penalties for violating the order render the guidelines meaningless. "I think it would be open, whether it was legal or not," says German, the former FBI agent. "Because we don't have all the facts about how they're doing it. For a long time, the NSA has been interpreting their authority in the broadest possible way, even beyond what an objective observer would say was reasonable." "An American citizen has Fourth Amendment rights wherever they are," adds Kurt Opsahl, an attorney with the Electronic Frontier Foundation. "Nevertheless, there have certainly been a number of things published over the last year which suggest that there are broad, sweeping programs that the NSA and other government agencies are doing abroad that sweep up the communications of Americans." Legal or not, the NSA's covert surveillance of an entire nation suggests that it will take more than the president's tepid "limits" to rein in the ambitions of the intelligence community. "It's almost like they have this mentality -- if we can, we will," says German. "There's no analysis of the long-term risks of doing it, no analysis of whether it's actually worth the effort, no analysis of whether we couldn't take those resources and actually put them on real threats and do more good." It's not surprising, German adds, that the government's covert program in the Bahamas didn't remain covert. "The undermining of international law and international cooperation is such a long-term negative result of these programs that they had to know would eventually be exposed, whether through a leak, whether through a spy, whether through an accident," he says. "Nothing stays secret forever. It really shows the arrogance of these agencies -- they were just going to do what they were going to do, and they weren't really going to consider any other important aspects of how our long-term security needs to be addressed." [1] http://www.washingtonpost.com/world/national-security/nsa-surveillance-program-reaches-into-the-past-to-retrieve-replay-phone-calls/2014/03/18/226d2646-ade9-11e3-a49e-76adc9210f19_story.html [2] https://www.documentcloud.org/documents/1164079-02may2013-sso.html [3] https://www.documentcloud.org/documents/1164087-mystic.html [4] https://www.documentcloud.org/documents/1164086-sso-dictionary-excerpt.html [5] https://www.documentcloud.org/documents/1164088-somalget.html [6] https://www.documentcloud.org/documents/1164085-sidtoday-dea-the-other-warfighter.html [7] http://www.unodc.org/pdf/lap_mlaeg_report_final.pdf [8] http://www.vertic.org/media/National Legislation/Bahamas/BS_Listening_Devices_Act_1972.pdf [9] http://www.lexbahamas.com/Data Protection 2003.pdf [10] http://www.marketsandmarkets.com/Market-Reports/lawful-interception-market-1264.html [11] https://www.documentcloud.org/documents/1164087-mystic.html [12] https://www.documentcloud.org/documents/1164084-black-budget.html [13] http://www.reuters.com/article/2013/08/05/us-dea-sod-idUSBRE97409R20130805 [14] http://www.usatoday.com/story/news/nation/2013/08/05/justice-dea-special-operations-shield/2620439/ [15] http://www.whitehouse.gov/the-press-office/2014/01/17/presidential-policy-directive-signals-intelligence-activities [16] http://www.archives.gov/federal-register/codification/executive-order/12333.html [17] http://www.fas.org/irp/nsa/standards.html