https://firstlook.org/theintercept/2014/04/04/cuban-twitter-scam-social-media-tool-disseminating-government-propaganda/ The "Cuban Twitter" Scam Is a Drop in the Internet Propaganda Bucket By Glenn Greenwald 4 Apr 2014 This week, the Associated Press exposed a secret program [1] run by the U.S. Agency for International Development to create "a Twitter-like Cuban communications network" [2] run through "secret shell companies" in order to create the false appearance of being a privately owned operation. Unbeknownst to the service's Cuban users was the fact that "American contractors were gathering their private data in the hope that it might be used for political purposes"--specifically, to manipulate those users in order to foment dissent in Cuba and subvert its government. According to top-secret documents published today by The Intercept, this sort of operation is frequently discussed at western intelligence agencies, which have plotted ways to covertly use social media for "propaganda," "deception," "mass messaging," and "pushing stories." These ideas--discussions of how to exploit the internet, specifically social media, to surreptitiously disseminate viewpoints friendly to western interests and spread false or damaging information about targets--appear repeatedly throughout the archive of materials provided by NSA whistleblower Edward Snowden. Documents prepared by NSA and its British counterpart GCHQ--and previously published by The Intercept [3] as well as some by NBC News [4]--detailed several of those programs, including a unit devoted in part to "discrediting" the agency's enemies with false information spread online. The documents in the archive show that the British are particularly aggressive and eager in this regard, and formally shared their methods with their U.S. counterparts. One previously undisclosed top-secret document [5]--prepared by GCHQ for the 2010 annual "SIGDEV" gathering of the "Five Eyes" surveillance alliance comprising the UK, Canada, New Zealand, Australia, and the U.S.--explicitly discusses ways to exploit Twitter, Facebook, YouTube, and other social media as secret platforms for propaganda.
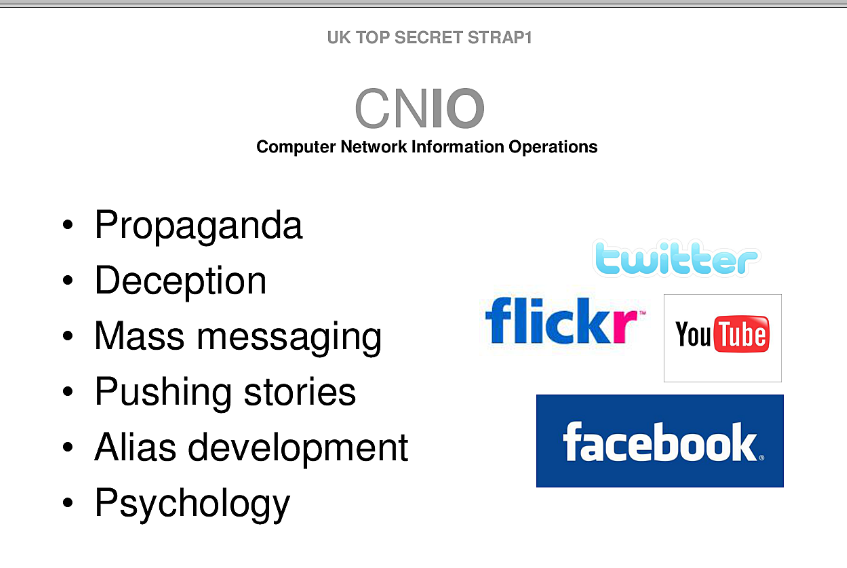 The document was presented by GCHQ's Joint Threat Research Intelligence Group (JTRIG). The unit's self-described purpose is "using online techniques to make something happen in the real or cyber world," [6] including "information ops (influence or disruption)." The British agency describes its JTRIG and Computer Network Exploitation operations as a "major part of business" at GCHQ, conducting "5% of Operations."
The annual SIGDEV conference, according to one NSA document published today [7] by The Intercept, "enables unprecedented visibility of SIGINT Development activities from across the Extended Enterprise, Second Party and US Intelligence communities." The 2009 Conference, held at Fort Meade, included "eighty-six representatives from the wider US Intelligence Community, covering agencies as diverse as CIA (a record 50 participants), the Air Force Research Laboratory and the National Air and Space Intelligence Center."
Defenders of surveillance agencies have often insinuated that such proposals are nothing more than pipe dreams and wishful thinking on the part of intelligence agents. But these documents are not merely proposals or hypothetical scenarios. As described by the NSA document published today, the purpose of SIGDEV presentations is "to synchronize discovery efforts, share breakthroughs, and swap knowledge on the art of analysis."
For instance: One of the programs described by the newly released GCHQ document is dubbed "Royal Concierge," under which the British agency intercepts email confirmations of hotel reservations to enable it to subject hotel guests to electronic monitoring. It also contemplates how to "influence the hotel choice" of travelers and to determine whether they stay at "SIGINT friendly" hotels. The document asks: "Can we influence the hotel choice? Can we cancel their visit?"
Previously, der Spiegel [8] and NBC News both independently confirmed that the "Royal Concierge" program has been implemented and extensively used. The German magazine reported that "for more than three years, GCHQ has had a system to automatically monitor hotel bookings of at least 350 upscale hotels around the world in order to target, search, and analyze reservations to detect diplomats and government officials." NBC reported that "the intelligence agency uses the information to spy on human targets through 'close access technical operations,' which can include listening in on telephone calls and tapping hotel computers as well as sending intelligence officers to observe the targets in person at the hotels."
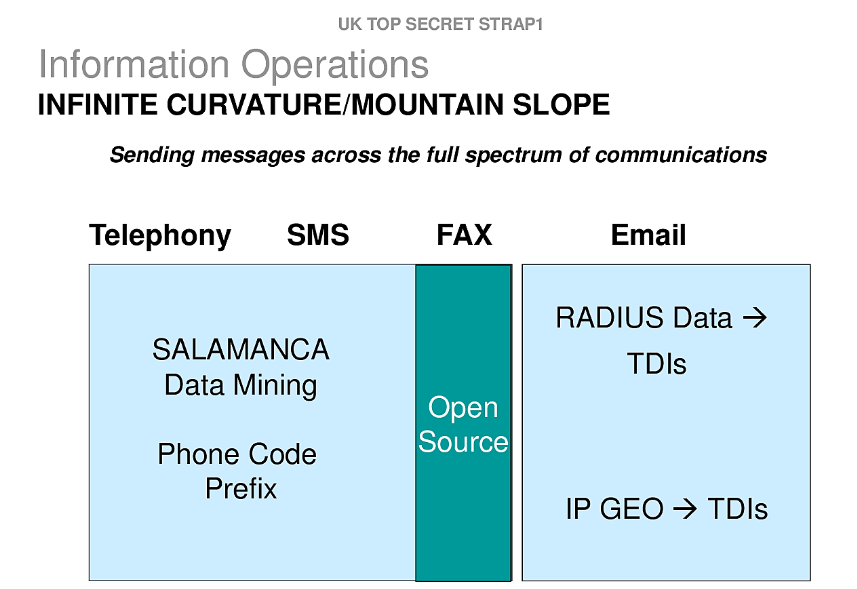
The GCHQ document we are publishing today expressly contemplates exploiting social media venues such as Twitter, as well as other communications venues including email, to seed state propaganda--GHCQ's word, not mine--across the internet:
The document was presented by GCHQ's Joint Threat Research Intelligence Group (JTRIG). The unit's self-described purpose is "using online techniques to make something happen in the real or cyber world," [6] including "information ops (influence or disruption)." The British agency describes its JTRIG and Computer Network Exploitation operations as a "major part of business" at GCHQ, conducting "5% of Operations."
The annual SIGDEV conference, according to one NSA document published today [7] by The Intercept, "enables unprecedented visibility of SIGINT Development activities from across the Extended Enterprise, Second Party and US Intelligence communities." The 2009 Conference, held at Fort Meade, included "eighty-six representatives from the wider US Intelligence Community, covering agencies as diverse as CIA (a record 50 participants), the Air Force Research Laboratory and the National Air and Space Intelligence Center."
Defenders of surveillance agencies have often insinuated that such proposals are nothing more than pipe dreams and wishful thinking on the part of intelligence agents. But these documents are not merely proposals or hypothetical scenarios. As described by the NSA document published today, the purpose of SIGDEV presentations is "to synchronize discovery efforts, share breakthroughs, and swap knowledge on the art of analysis."
For instance: One of the programs described by the newly released GCHQ document is dubbed "Royal Concierge," under which the British agency intercepts email confirmations of hotel reservations to enable it to subject hotel guests to electronic monitoring. It also contemplates how to "influence the hotel choice" of travelers and to determine whether they stay at "SIGINT friendly" hotels. The document asks: "Can we influence the hotel choice? Can we cancel their visit?"
Previously, der Spiegel [8] and NBC News both independently confirmed that the "Royal Concierge" program has been implemented and extensively used. The German magazine reported that "for more than three years, GCHQ has had a system to automatically monitor hotel bookings of at least 350 upscale hotels around the world in order to target, search, and analyze reservations to detect diplomats and government officials." NBC reported that "the intelligence agency uses the information to spy on human targets through 'close access technical operations,' which can include listening in on telephone calls and tapping hotel computers as well as sending intelligence officers to observe the targets in person at the hotels."
The GCHQ document we are publishing today expressly contemplates exploiting social media venues such as Twitter, as well as other communications venues including email, to seed state propaganda--GHCQ's word, not mine--across the internet:

 (The GCHQ document also describes a practice called "credential harvesting," which NBC described as an effort to "select journalists who could be used to spread information" that the government wants distributed. According to the NBC report, GCHQ agents would employ "electronic snooping to identify non-British journalists who would then be manipulated to feed information to the target of a covert campaign." Then, "the journalist's job would provide access to the targeted individual, perhaps for an interview." Anonymous sources that NBC didn't characterize claimed at the time that GCHQ had not employed the technique.)
Whether governments should be in the business of publicly disseminating political propaganda at all is itself a controversial question. Such activities are restricted by law in many countries, including the U.S. In 2008, The New York Times' David Barstow won a Pulitzer Prize for exposing a domestic effort [9] coordinated by the Pentagon whereby retired U.S. generals posed as "independent analysts" employed by American television networks and cable news outlets as they secretly coordinated their messaging with the Pentagon.
Because American law bars the government from employing political propaganda domestically, that program was likely illegal, [10] though no legal accountability was ever brought to bear (despite all sorts of calls [11] for formal investigations [12]). Barack Obama, a presidential candidate at the time, pronounced himself in a campaign press release "deeply disturbed" by the Pentagon program, which he said "sought to manipulate the public's trust."
Propagandizing foreign populations has generally been more legally acceptable. But it is difficult to see how government propaganda can be segregated from domestic consumption in the digital age. If American intelligence agencies are adopting the GCHQ's tactics of "crafting messaging campaigns to go 'viral'," the legal issue is clear: A "viral" online propaganda campaign, by definition, is almost certain to influence its own citizens as well as those of other countries.
For its part, GCHQ refused to answer any specific questions on the record, instead providing its standard boilerplate script which it provides no matter the topic of the reporting: "all of GCHQ's work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorised, necessary and proportionate, and that there is rigorous oversight." The NSA refused to comment.
But these documents, along with the AP's exposure of the sham "Cuban Twitter" program, underscore how aggressively western governments are seeking to exploit the internet as a means to manipulate political activity and shape political discourse.
Those programs, carried out in secrecy and with little accountability (it seems nobody in Congress knew of the "Cuban Twitter" program in any detail) threaten the integrity of the internet itself, as state-disseminated propaganda masquerades as free online speech and organizing. There is thus little or no ability for an internet user to know when they are being covertly propagandized by their government, which is precisely what makes it so appealing to intelligence agencies, so powerful, and so dangerous.
[1] http://news.yahoo.com/white-house-defends-cuban-twitter-stir-unrest-222510641.html
[2] http://www.npr.org/templates/story/story.php?storyId=298902488
[3] https://firstlook.org/theintercept/2014/02/24/jtrig-manipulation/
[4] http://www.nbcnews.com/news/investigations/snowden-docs-british-spies-used-sex-dirty-tricks-n23091
[5] https://firstlook.org/theintercept/document/2014/04/04/full-spectrum-cyber-effects/
[6] https://firstlook.org/theintercept/2014/02/24/jtrig-manipulation/
[7] https://firstlook.org/theintercept/document/2014/04/04/2009-sigdev-conference/
[8] http://www.spiegel.de/international/europe/gchq-monitors-hotel-reservations-to-track-diplomats-a-933914.html
[9] http://www.nytimes.com/2008/04/20/us/20generals.html
[10] http://www.prwatch.org/node/7261
[11] http://utdocuments.blogspot.com.br/2008/04/letters-from-rep-rosa-delauro-to.html
[12] http://www.huffingtonpost.com/ari-melber/clinton-and-obama-finally_b_98994.html
(The GCHQ document also describes a practice called "credential harvesting," which NBC described as an effort to "select journalists who could be used to spread information" that the government wants distributed. According to the NBC report, GCHQ agents would employ "electronic snooping to identify non-British journalists who would then be manipulated to feed information to the target of a covert campaign." Then, "the journalist's job would provide access to the targeted individual, perhaps for an interview." Anonymous sources that NBC didn't characterize claimed at the time that GCHQ had not employed the technique.)
Whether governments should be in the business of publicly disseminating political propaganda at all is itself a controversial question. Such activities are restricted by law in many countries, including the U.S. In 2008, The New York Times' David Barstow won a Pulitzer Prize for exposing a domestic effort [9] coordinated by the Pentagon whereby retired U.S. generals posed as "independent analysts" employed by American television networks and cable news outlets as they secretly coordinated their messaging with the Pentagon.
Because American law bars the government from employing political propaganda domestically, that program was likely illegal, [10] though no legal accountability was ever brought to bear (despite all sorts of calls [11] for formal investigations [12]). Barack Obama, a presidential candidate at the time, pronounced himself in a campaign press release "deeply disturbed" by the Pentagon program, which he said "sought to manipulate the public's trust."
Propagandizing foreign populations has generally been more legally acceptable. But it is difficult to see how government propaganda can be segregated from domestic consumption in the digital age. If American intelligence agencies are adopting the GCHQ's tactics of "crafting messaging campaigns to go 'viral'," the legal issue is clear: A "viral" online propaganda campaign, by definition, is almost certain to influence its own citizens as well as those of other countries.
For its part, GCHQ refused to answer any specific questions on the record, instead providing its standard boilerplate script which it provides no matter the topic of the reporting: "all of GCHQ's work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorised, necessary and proportionate, and that there is rigorous oversight." The NSA refused to comment.
But these documents, along with the AP's exposure of the sham "Cuban Twitter" program, underscore how aggressively western governments are seeking to exploit the internet as a means to manipulate political activity and shape political discourse.
Those programs, carried out in secrecy and with little accountability (it seems nobody in Congress knew of the "Cuban Twitter" program in any detail) threaten the integrity of the internet itself, as state-disseminated propaganda masquerades as free online speech and organizing. There is thus little or no ability for an internet user to know when they are being covertly propagandized by their government, which is precisely what makes it so appealing to intelligence agencies, so powerful, and so dangerous.
[1] http://news.yahoo.com/white-house-defends-cuban-twitter-stir-unrest-222510641.html
[2] http://www.npr.org/templates/story/story.php?storyId=298902488
[3] https://firstlook.org/theintercept/2014/02/24/jtrig-manipulation/
[4] http://www.nbcnews.com/news/investigations/snowden-docs-british-spies-used-sex-dirty-tricks-n23091
[5] https://firstlook.org/theintercept/document/2014/04/04/full-spectrum-cyber-effects/
[6] https://firstlook.org/theintercept/2014/02/24/jtrig-manipulation/
[7] https://firstlook.org/theintercept/document/2014/04/04/2009-sigdev-conference/
[8] http://www.spiegel.de/international/europe/gchq-monitors-hotel-reservations-to-track-diplomats-a-933914.html
[9] http://www.nytimes.com/2008/04/20/us/20generals.html
[10] http://www.prwatch.org/node/7261
[11] http://utdocuments.blogspot.com.br/2008/04/letters-from-rep-rosa-delauro-to.html
[12] http://www.huffingtonpost.com/ari-melber/clinton-and-obama-finally_b_98994.html